Subscriber Benefit
As a subscriber you can listen to articles at work, in the car, or while you work out. Subscribe NowAs the threat of cyberattacks continues to loom over professions including the law, legal practitioners are taking additional steps to protect themselves and their firms from harmful access to their data.
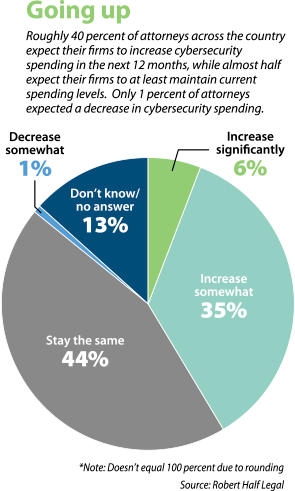
According to a recent survey released by Robert Half Legal, roughly 41 percent of all attorneys expect their firms to increase their cybersecurity spending in the next 12 months. Similarly, about 44 percent will maintain their current funding levels, while only 1 percent indicated an expected cut in resources devoted to technological protection.
The expected increase in cybersecurity spending doesn’t come as a surprise to local law firm chief information officers or cybersecurity experts. There is no way any firm or legal organization can completely protect itself against hackers or other cybercriminals, the experts said, but firms can — and do — take additional steps to lessen the threat.
 Staying up-to-date
Staying up-to-date
At Taft Stettinius & Hollister LLP, those steps include basic computer protection software that filters emails for spam, phishing attacks, malicious URLs, ransomware, and the like, said CIO John Carroll. The Indianapolis-based firm also works with third-party security experts to evaluate the threat landscape and determine what additional protections are most appropriate for its needs.
That landscape is constantly evolving, which means Carroll is continuously evaluating what cybersecurity tools will be the most relevant. Next year, for example, he’s planning on rolling out a new tool that conducts a behavioral pattern
analysis to detect malicious emails or other attacks that may have gotten through filters.
While it’s important to continuously evaluate a firm’s cybersecurity practices as threats evolve in a manner similar to what Carroll does, it’s also critical to ensure existing protections remain up-to-date and relevant, said Fred Cate, vice president for research at Indiana University. In addition to concerns about diminished effectiveness as cybersecurity technology ages, using out-of-date software also presents legal ethics issues related to competency, he said.
 Reynolds
ReynoldsStephen Reynolds, co-chair of Ice Miller LLP’s Data Security and Privacy Practice, agreed. He pointed to recent guidance from the American Bar Association and Association of Corporate Counsel that called on attorneys to take necessary precautions to protect client data. The Indiana Supreme Court in July amended Rule of Professional Conduct 1.1 concerning competency to require attorneys to be aware of “the benefits and risks associated with the technology relevant to the lawyer’s practice.” The amendment takes effect Jan. 1, 2018.
Such requirements make it clear that the legal industry places high value on effective and up-to-date cybersecurity practices, which is part of the driving force behind firms’ decisions to devote more resources to cybersecurity spending, Reynolds said.
Similarly, when a law firm data breach does occur and a client decides to sue, it is unlikely a firm could convince a judge it had done all in its power to protect the breached data if the protection software was not current, Cate said.
“It’s hard to think of anything worse for a law firm than having clients’ secrets made public,” he said.
Proactive or reactive?
 Biederman
BiedermanWhile making the decision to spend more money on cybersecurity practices may seem like an indication that lawyers are taking a more proactive approach to their data, Ray Biederman, founding partner of Mattingly Burke Cohen & Biederman LLP, said the legal industry is still reactive to cyberthreats in many ways. Specifically, Biederman pointed to pressure from clients to protect their data as a likely driving force behind the increased cybersecurity spending. He speculated that firms may be reacting to client demands more than proactively protecting against attacks.
Further, the number of cybersecurity firms that can offer services to lawyers is increasing, which means legal organizations are reacting to marketing from those cybersecurity firms and taking them up on their offer to proactively defend against attacks, Biederman said.
Even so, John McCauley, a partner at Bingham Greenebaum Doll LLP and a certified information privacy professional, said there are also indications the legal industry is transitioning to a more proactive approach to protecting its data that is similarly driven by client needs. From a business perspective, it makes sense to be able to tell potential clients that a firm has adequate security measures in place so that they feel safe entrusting their data to that firm, he said.
Similarly, it’s important to be able to assure clients there is a plan in place should a breach occur, McCauley said, noting it’s equally as necessary to have plans for protecting against and responding to attacks. McCauley also stressed the importance of all parties understanding their role in a response plan, as the plan will not effectively restore lost data or access if even one party fails to fulfill their duty.
“It’s like a fire drill policy — if you don’t go through the physical process, it’s pretty much worthless,” he said.
Avoiding human error
But it’s not only important for attorneys to understand what to do when a breach occurs, the experts said — they also have to know how to recognize and defend against attacks on their personal computers.
While the phrase “cybersecurity spending” is traditionally associated with technology and software, Cate said allocating resources to human training is at least as important. Reynolds agreed, noting that law firms often do not devote sufficient resources to training to their attorneys and support staff.
There are multiple ways legal organizations can ensure their employees are taking the necessary cybersecurity precautions, the first of which is providing basic training on what those practices entail.
At Taft, Carroll said his goal in offering cybersecurity training to the firm’s attorneys is to create a culture in which the attorneys feel comfortable asking for help when they are unsure if they are being spammed or attacked. Along similar lines, McCauley suggested sending out a “test” email attack that measures how many recipients click on the test link or URL, then following up to show them the signs they missed that indicated they should not have clicked.
There’s also a threat of “malicious insiders” who use their legitimate access to a firm’s data to steal company secrets or participate in insider trading. Reynolds noted that attorneys who work with mergers and acquisitions can be particularly susceptible to cyberthreats for insider trading purposes.
To guard against threats of that nature, McCauley recommended removing a person’s access to data that is not relevant to their job, and terminating access as soon as an employee leaves a firm.
Using common sense
Even though many attorneys who responded to the Robert Half Legal survey indicated their firms were committed to stronger cybersecurity practices, Cate expressed concern about the fact that roughly 60 percent of respondents did not indicate they would not be increasing their cybersecurity spending. He speculated that firms that do not intend to devote more resources to protecting data may not be fully aware of the threat against them, noting that there are two types of law firms in today’s digital world: those that have been hacked and are aware, and those that have been hacked and are not aware.
Failing to take adequate precautions to protect against those inevitable attacks has become the equivalent of legal malpractice, Cate said, so firms can no longer ignore the need to continuously evaluate and enhance their protective measures. Biederman agreed, noting that common sense about the digitization of the practice of law points to the need for extra caution.
“Someone wouldn’t open up their mail and leave it sitting outside and expect nothing to happen,” Biederman said. “We should have the same sort of common sense approach to electronic data.”•
Please enable JavaScript to view this content.

